Sean Gallagher of Ars Technica reports (“WannaCry? Hundreds of US schools still haven’t patched servers“) that two years after Microsoft published security patches to address the issue hundreds of U.S. K-12 schools still haven’t fixed vulnerabilities at the root of WannaCry ransomware and its variants. From the story:
“There are hundreds of thousands of Internet-connected Windows systems in the United States that still appear to be vulnerable to an exploit of Microsoft Windows’ Server Message Block version 1 (SMB v. 1) file sharing protocol, despite repeated public warnings to patch systems following the worldwide outbreak of the WannaCry cryptographic malware two years ago. And based on data from the Shodan search engine and other public sources, hundreds of them—if not thousands—are servers in use at US public school systems.”
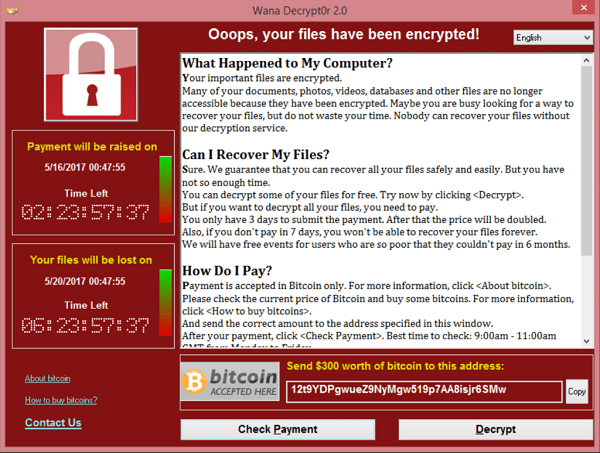
“Furthermore, the fact that these systems remain unpatched a full two years after WannaCry—and after Microsoft pushed out emergency patches for even no-longer-supported operating systems—raises the question as to what other critical security patches these organizations didn’t patch.”
Among the school districts running the exploitable Microsoft products, the Ars Technica article specifically calls out (and apparently attempted to contact):
- Baltimore County (MD) Public Schools
- Montebello (CA) Unified School District
- Fresno Unified (CA) School District
- The Washington (WA) School Information Processing Cooperative
- Cupertino (CA) Union School District
Less than half way through 2019, the K-12 Cyber Incident Map has already identified 13 incidents related to ransomware and malware outbreaks in school districts. Many of these could have been avoided if the security of school IT systems were maintained per the recommendations of their developers, including by installing freely available security patches.
There’s no time like the present to act if you suspect your district may be among those that remain vulnerable.