Emerging Lessons from the K-12 Cyber Incident Map
[Cross-posted at https://ferpasherpa.org/levin1/ on FERPA|Sherpa, the education privacy resource center of Future of Privacy Forum (FPF). Thanks to Amelia Vance, FPF Education Policy Counsel, for the invitation to contribute.]
As K-12 schools grow increasingly reliant on digital tools and services for teaching, learning, and other core services, they can maintain and build trust with their local communities by ensuring sensible privacy protections for students, educators, and other school staff. While this is fundamentally hard and important work, it also is insufficient if reasonable school information security practices are not enacted in concert with privacy protections.
Cyber incidents perpetrated against schools can result in the disclosure of personal information and identity theft, the loss of taxpayer dollars, and the loss of instructional time.
Indeed, if there is an Achilles’ heel to a future of robust personalized learning for all K-12 students, it is the uneven attention to the cybersecurity risks facing school information technology assets and data. Even in cases where ‘cyber incidents’ do not result in the unauthorized disclosure of personal information, they accrue real costs to schools in responding – such as school staff time spent investigating incidents, responding to parents and the press, and restoring files from backups or instituting new technical safeguards – and undermine the trust of communities in the ability of schools and their service providers to manage personal information in a digital teaching and learning environment.
The Landscape of School Cyber Threats
Based on the data collected in creating the K-12 Cyber Incident Map, over the last 17 months at least 141 U.S. K-12 schools and districts have been the subject of one or more publicly disclosed cyber incidents.** As shown in the accompanying figure, these incidents include: (a) phishing attacks resulting in the disclosure of personal data; (b) other unauthorized disclosures, breaches or hacks resulting in the disclosure of personal data; (c) ransomware attacks; (d) denial-of-service attacks; and (e) other cyber incidents resulting in school disruptions and unauthorized disclosures.
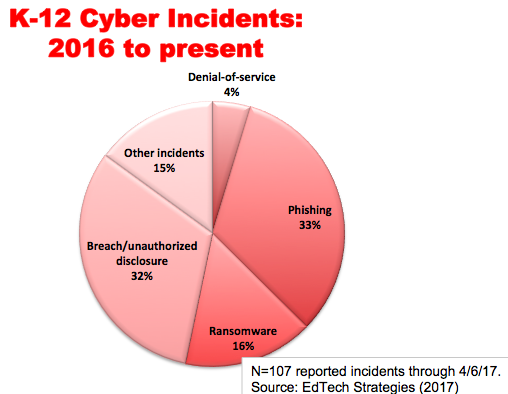

I suggest that three lessons, however tentative, can be drawn from the emerging map of cyber threats facing K-12 schools:
First, schools appear to experiencing an increasing number of cyber incidents. A total of 67 incidents were reported during 2016; 74 have been reported so far in the first 5 months of 2017. If this pace continues, it will represent over a 100 percent increase in reported incidents in 2017 over last year. While there could be a number of reasons to explain this concerning trend, in general one would expect more frequent cyber incidents in schools as their reliance on technology increases. Indeed, there is no reason to believe that the K-12 education sector is or will be immune to the digital threats facing other sectors of the economy that similarly rely on data, analytics, and information systems for their operations.
Second, the range of cyber threats affecting schools appears to be diverse and shifting over time. For instance, the first five months of 2017 have seen a dramatic spike in targeted phishing attacks against school districts. There were a total of 8 reported phishing attacks against schools in 2016; so far in 2017, there already have been more than 4 times as many. And, while the perpetrator of a cyber incident is not always identified in public reports (if it is even known), a significant proportion of those perpetrators that are identified are so-called ‘insiders’ (i.e., educators, school staff, and students themselves). This suggests that any effective response to school cybersecurity concerns must account for both external threats from unknown black-hat hackers, as well as from internal threats from those who are themselves part of the school community.
School staff and students were directly responsible for about one in four cyber incidents perpetrated against K-12 schools that have been disclosed since 2016.
A related – but no less important – issue faces schools in deciding the appropriate circumstances, if any, to charge K-12 students as criminals when they are found to be the instigator or cause of a school cyber incident (as they were in half of the 36 cases reported to involve school insiders).
Third, in addition to concerns about student data privacy, personal data about school system employees is being targeted and also is at risk. In many communities, school districts are among the largest employers. As such, they represent an attractive target for identity theft. This year alone, via a clever social engineering attack, criminals have successfully phished tax-related information of thousands of school system employees from coast to coast, resulting in widespread identity theft. Just as sensitive information about the children and youth served in public schools deserves protection, so should reasonable protections be offered to those who choose to work for and in public schools.
Charting a Way Forward for Improved K-12 Information Security
If we are to maintain the privacy of sensitive information collected for and about the purposes of K-12 education, students, educators and families all must trust that schools – and their service providers – can reasonably safeguard that information. Yet, the data underlying the K-12 Cyber Incident Map provides evidence that schools may be facing an increasing challenge in doing so.
While I have previously outlined a number of elements that should be included in any meaningful policy framework for addressing these school cybersecurity challenges, the need for an enhanced data base of potentially meaningful school cybersecurity threats is perhaps most foundational of all. Issues of information technology security are related to and often confounded with privacy issues, and they can be challenging for school leaders and policymakers to respond to because of this complexity – especially in the absence of evidence.
Despite the fact that schools and their service providers may be reluctant to disclose these incidents for reasons both good and bad, we need comprehensive, current data on the variety, frequency, and severity of threats if we are to chart an informed (and cost-effective) way forward. Information security is a prerequisite to privacy – and now is the right time for education leaders to increase their focus on shoring up security policies and practices in K-12 schools.
** Based as it is primarily on public media reports of cyber incidents, the dataset underlying the K-12 Cyber Incident Map is incomplete, perhaps by orders of magnitude, and may contain errors. Neither school districts nor their vendors are compelled to make public disclosures of every potentially significant incident (if required at all by state data breach notification laws), and media reports can be short and ambiguous. It also is typical for there to be a significant gap in time (from months to years) between when a K-12 cyber incident occurs and when public reports are made.