K-12 Information Security Strategies: Research and Recommendations
Guest post by Dr. Travis Paakki, Senior Director, Office of Technology and Information Services, Portland (OR) Public Schools
I work at one of the top 100 largest districts in the country in terms of student enrollment, and like most school districts, we struggle with information security. Our IT department is under-resourced in a way that no similar-sized private industry business would even consider attempting. Strangely, though, I’d say we are lucky. In spite of such under-resourcing, we have dedicated information security staff, which is a lot more than many of the other nation’s districts could say.
Thanks to a barren regulatory landscape, IT and information security issues seldom get due attention unless (or until) a data breach of other major incident is experienced. Add to that the fact that district leaders often rise through the academic ranks and therefore have little exposure to the operational demands and liabilities of running a large, data-rich enterprise. As such, it should be no surprise that malicious hackers are coming to see the country’s school districts as appealing and easy targets.
Many of us in K-12 remember the FBI memo about K-12 information security released on September 13, 2018. The subsequent face-palm came near the end of the document after reading the recommendation that parents and families should contact their school systems to learn about information security measures. Some of us had good answers when they did so, others not so much. If it was a slow news day in your area, this one got phones ringing. Further, on Wednesday, July 24, Louisiana declared a state of emergency when three of its districts had their technology assets taken hostage in ransomware attacks. If K-12 lags even five years behind its private industry counterparts, we can expect these to continue for some time to come. The threats to our student and staff privacy, as well as our business and operations groups, are clear and well-documented.
For smaller districts, the issue can seem insurmountable. When reviewing the National Center for Education Statistics data on K-12 school districts, one of the critical problems plaguing K-12 information security becomes apparent: Approximately half of the nation’s K-12 students attend school districts where total enrollment is less than 10,000 students. This smaller student population means fewer resources for IT, including fewer – if any – dedicated security staff. Indeed, even in larger districts, information security is often a side-job and lacks the formality of a plan, proper funding, a framework to build on, and adequate measures for reporting.
But why?
Earlier research suggested that those responsible for information security in school districts had an appropriate amount of knowledge regarding information security best practices (Brown, 2016). One of the challenges information security professionals often face is getting the organization to understand that information security is not a technology problem, but rather one of culture and prioritization. My research (Paakki, 2019) focused on discovering what information security staff could do to improve information security and what I came to understand was something not altogether unexpected. Nonetheless, the findings were not explicitly stated elsewhere: K-12 lacks essential strategies for improving information security.
For my research, a strategy was generically defined as a method or plan which will bring about a desired future state. The definition could then refer to budgets, laws, culture, board and organizational structure, standard practices, ethical expectations, and others. Working with information security leaders from around the country, I was able to compose a picture of strategies that were essential to information security in other industries and then extrapolate that to apply to K-12. Those strategies included:
- Prescriptive laws, standards, and norms – FERPA is the K-12 go-to, and while helpful, it includes no mandates for information security roles, nor a viable penalty for a lack of due diligence. In the absence of a new law that may take years to come into effect, norms can be used to demand ethical behavior by district leaders. By establishing a K-12 industry norm for cybersecurity practices, information security can be elevated to where it should be. Not just in terms of minimum requirements to be compliant, but broadly in terms of the sets of actions and behaviors necessary to demonstrate ethical stewardship of data.
- Appropriate staffing and funding – Based on research from Gartner, information security should account for 5-7 percent of the overall IT budget, which itself should typically between 2-10 percent of the size of the entire organization’s budget (depending on the industry). In K-12, that overall IT number is usually 3-5 percent of larger district expenditures (Council of the Great City Schools, 2018). Also, understand that to stand up an effective information security practice, additional money will need to be spent first to build infrastructure and capacity before the 5-7 percent sized security team can perform sustaining operations.
- A culture of information security – Just as modern organizations request that staff members evaluate actions through an equity lens, staff must also employ an information security lens in their day-to-day work. Organizations with successful information security practices view it as a shared responsibility. In those organizations, information security efforts are promoted and endorsed by senior leadership so that all levels of staff within the organization understand its impact and importance, as well as underscoring the fact that information security is not and cannot be viewed as merely an IT issue.
- Use of a security framework – The NIST Cybersecurity Framework or the CIS Controls are tremendous resources for setting information security targets for an organization and assessing progress towards those targets. Every subject in my research had at least one framework that they assessed their organizations against and found it vital to communicating the “why” of the money and resources they were requesting, as well as the “what” of directing the team’s work.
- Augmenting security staff – In all cases, the definition of what is and is not considered information security varied. For instance, is anti-virus part of the desktop group or the security group? Are firewalls a network team responsibility or a security team responsibility? Augmenting security functions by creating dotted-line relationships, supplemented with managed security service providers, is a way to track security responsibilities without creating impossible staffing obligations. Additionally, as cyber risk insurance policies evolve, pre-incident audit and post-incident response and remediation coverage can serve as advocacy and capability for constrained security teams.
- Leveraging auditors and transparency mechanisms – Auditors are the best way to garner an informed, impartial voice supporting the efforts of the security organization. By assessing against the chosen framework, auditors can recommend and aid in prioritization of what work needs to happen next. All of this reduces the burden on transparency and reporting from the security leader.
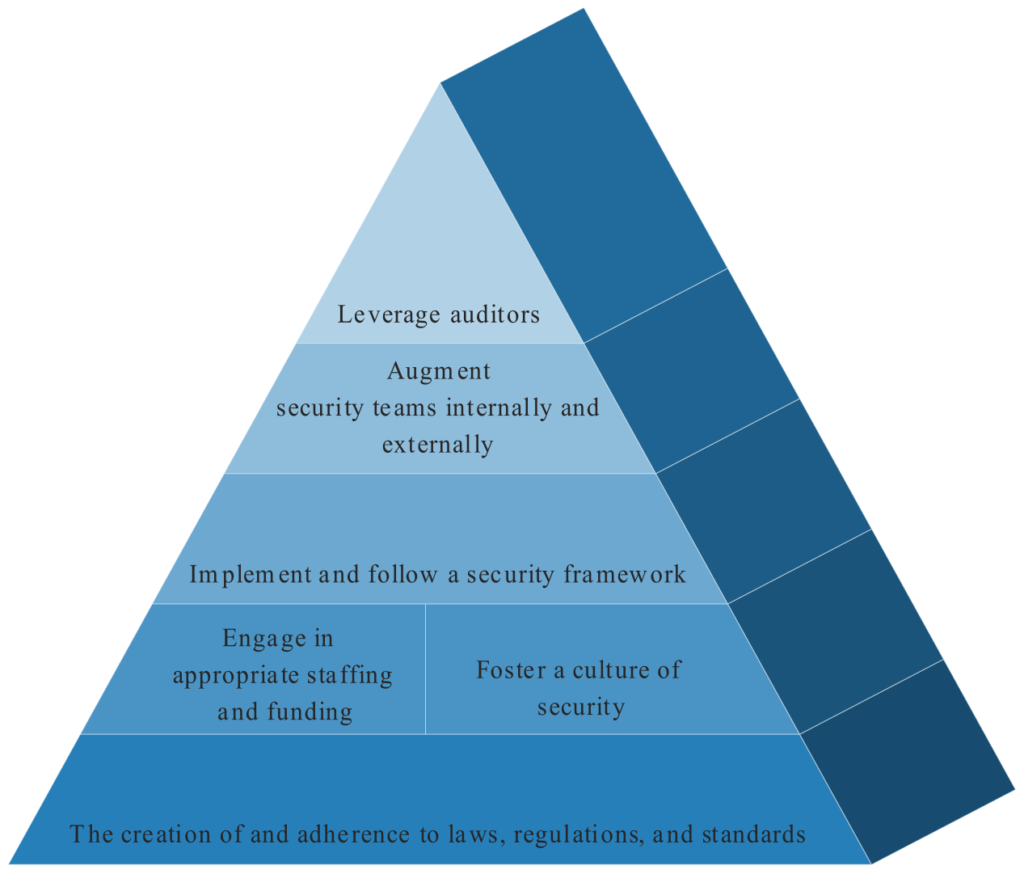
The result: an interdependent set of information security strategies essential to school IT security success (see illustration above). It is comprised of a foundational set of strategic layers that each subsequent layer could then be constructed. As an example, staffing and funding, and a culture of security exist in the scope of the laws, regulations, and standards of the organization. A security framework implementation is dependent on the staffing, funding, and culture of the organization, and so on. This structure forms a pyramid of layered strategies necessary for the improvement of information security in a school district.
Informing Stakeholders
Based on my research, I compiled a checklist for board members and administrators to review with their IT staff. If strategies were found to be lacking, district leadership could direct resources to fund them accordingly. Parents and families, for instance, could ask if districts have implemented some or any of the strategies to address student data privacy concerns. For each of the stakeholder groups, it is important to instill a drive to implement these strategies:
- Administrators need to respect the idea that they are not just running academic institutions. They are also running unbelievably complex businesses, with computerized operational systems containing sensitive information. If they don’t understand these functions, they must appoint those that do. Also, they must insist on reporting both to leadership and the public to prove those appointees understand and act as responsible, ethical stewards of the data and the school systems in their care. Administrators need to embrace that information security is a cultural and people issue, not a technology one, and they must champion security efforts. Also, administrators must ensure that funding needs to be available for reasonable protection of district data and resources.
- Board members need to insist that budgets are allocated in a way that not only addresses the educational needs of the students, but also protects student and staff data privacy and district assets from being compromised in a costly cyber breach. They need to demand reasonable transparency and force the district to address problems in a timely fashion.
- Parents and families can range in skill from the talented information security professional to the completely inexperienced. All of them have a vested interest in the safety of their children’s information, and that district funds are spent wisely. They need to use their influence to ensure that all the other stakeholders listed here engage appropriately using their voices and votes.
- Lawmakers have ignored K-12 education. FERPA and its amendments are a start, but the law is woefully out of date, and state laws often focus on vendor obligations. Laws should be enacted that dictate student ownership of data and the obligations of districts to protect the data with which they are entrusted. Those laws must have designated responsible parties for information security, senior leadership accountability, and viable punitive repercussions for a lack of compliance. These are long overdue and will force districts to prioritize spending and staffing properly.
- Industry can choose to engage in a low-margin, high-volume market like K-12 by supporting outsourcing at a district, regional, or state level. Additionally, local businesses can combine efforts to create a SOC that can service area districts using staff and resources they donate towards the effort as a way to build their own staff’s skills and populate a pipeline of future staffing options.
The Requirements of the Smaller Districts
Now I come back to the districts that enroll 9,999 students or fewer. Can smaller and more rural districts be expected to maintain staff to address information security? Much like the case with HIPAA, the answer is, “yes.” They are required to protect data because they have it, and there should be no sliding scale of liability based on size. That said, there is no way small districts can adequately address information security obligations with only in-house expertise. These organizations must seek ways to share and/or transfer that risk to organizations that are better equipped to perform these expert tasks. Volunteers, educational service districts, managed security services providers, and/or consortia of districts with similar needs can help small districts to collectively address their information security needs, but they must be obliged to do so. Whatever the solution, saying “we can’t afford security” can no longer be an excuse.
What’s next?
A lot. It was surprising to only be able to identify a comparatively few resources about K-12 information security versus almost any other industry I examined. Rather than delving into this enormous topic in this already lengthy post, I will open the conversation with the following:
- Education – Superintendents and administrators need to be taught technology awareness and information security fluency as a part of the basic educational requirements associated with getting their credentials. The board and public should also be educated through annual reporting on the state of their schools’ information security posture so they can demand resolution or at the very least, a plan. As always, it is our role to provide education to those that are willing to listen.
- Advocacy – Now is the time to work with senators and congressional representatives to ensure that school funds are increased to deal with the obligations for information security. You can insist that privacy legislation mandates the creation of a district information security program, names a person responsible for information security, establishes viable penalties, and mandates reporting on the health of such programs.
- Action – I will be repeating my findings to any administrator who will listen. I ask that you do the same. We in the K-12 information security space should create achievable information security plans, and report on progress towards their milestones. Demonstrate good security practices, and raise a brave voice when you witness a bad practice or situation which puts the district at risk. Too often, we allow ourselves to be the keeper of the knowledge about vulnerabilities and issues. Sharing that information not only informs but transfers some of the risk for inaction to those who should be owning it.
The 50+ million students in our nation’s schools deserve to have their information protected. With your help, we can address this looming crisis. We can demand that the districts in this country treat their vital business systems – and the student and staff data they contain – with the same reverence and due care that a private industry counterpart does. We must do this to make sure that today’s students enter society with clean slates and that the staff that serves them can focus on their education.
Dr. Travis Paakki has worked in Education Technology for 10 years. He has focused on Information Assurance, ERP systems, and Architecture. He holds a Bachelor’s of Science in Computer Science with a specialization in Information Security and an MBA with a focus on IT Management from Western Governors University, and a doctorate in Computer Science with a focus on Information Assurance from Colorado Technical University. He works for Portland Public Schools as the Senior Director of the Office of Technology and Information Systems.