NOTE: School district IT teams interested in benchmarking their cybersecurity policies and practices can now do so by taking the free, NIST CSF aligned K-12 Cybersecurity Self-Assessment (available online at: https://k12cybersecure.com/resources/k-12-cybersecurity-self-assessment/
Guide to the NIST Cybersecurity Framework: A K-12 Perspective
Guest post by April Mardock, Information Security Manager, Seattle Public Schools
You may have heard about the NIST Cybersecurity Framework, but what exactly is it?
The National Institute for Standards and Technology (NIST) was tasked to create a “a prioritized, flexible, repeatable, performance based, and cost-effective approach, including information security measures and controls that may be voluntarily adopted by owners and operators of critical infrastructure to help them identify, assess, and manage cyber risks” in the Cybersecurity Enhancement Act of 2014.
K-12 is not technically critical infrastructure, but the framework can be easily adapted to the school district environment (including from sources such as the FTC’s “Understanding the NIST Cybersecurity Framework,” which this post is adapted from).
K-12 threats include (but are not limited to):
- Disruptions to school or central operations (examples include Spring Lake Park Schools (MN), Bigfork Public Schools (MT), Horry County Schools (SC), Rhinebeck Central School District (NY), and Swedesboro-Woolwich School District (NJ) all damaged with ransomware)
- Harms to individual staff or students (examples include the “Are you Available phish”)
- Hijacks of district resources, like systems, networks and data (examples include bitcoin mining operations in schools and IoT botnet infections)
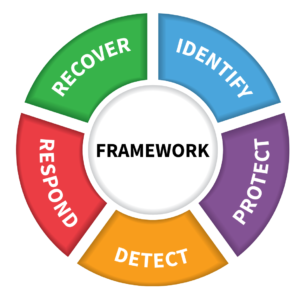
WHAT CAN YOUR DISTRICT DO?
1. IDENTIFY
- Make a list of all equipment, software, and data you use, including laptops, smartphones, tablets, and point-of-sale devices.
- Make a list of all vendors and vendor accounts that have access to district systems.
- Identify roles and responsibilities for employees, vendors, and anyone else with access to sensitive data.
- Identify steps to take to protect against an attack and limit the damage if one occurs, including the creation of an incident management plan.
- Identify the gaps and prioritize your current vulnerabilities and weaknesses, ranking them relative to the actual level of concern. Worry Index = %impact x %probability
- Identify and address the privacy implications of identity management and access control measures to the extent that they involve collection, disclosure, or use of personal information.
- Create and share a district cybersecurity handbook.
- Explicitly manage the on-boarding and off-boarding of employee accounts. Force removal and disabling of exited employee credentials and recovery of assets.
- Update your relevant school board policies for employee and student records to address data privacy, confidentiality, and accountability.
2. PROTECT
- Control and track who logs on to your network and uses your computers and other devices.
- Create a process for disabling potentially compromised accounts globally.
- Collect and centralize the logs.
- Change your purchase process to make cybersecurity part of your intake process. Modify RFP evaluation templates. Update contract and MoU templates to include cybersecurity language and concerns.
- Encrypt sensitive data, at rest and in transit. Protect your API and encryption keys. Encrypt laptops and USB drives with offline data to protect against theft and loss.
- Conduct regular backups of data. Test the backups.
- Schedule application, operating system (OS), and firmware updates regularly, automating those patches where possible.
- Have formal policies for safely disposing of electronic files and old devices, including printers.
- Partition your networks into smaller pieces.
- Make sure you have enabled all malware protections in your web filters.
- Limit the use of Domain Admin and other sensitive accounts to as needed ONLY, and force multi-factor authentication (MFA) for sensitive accounts.
- Use different admin passwords for staff, students, and servers. Change them periodically.
- Train everyone who uses your computers, devices, and network about cybersecurity. You can help employees understand their personal risk in addition to their crucial role in the workplace.
![]() 3. DETECT
3. DETECT
- Monitor your computers and web use for unauthorized personnel access, devices (like USB drives), software, and shadow IT data uses like Dropbox, Google Drive, Box and ShareFile.
- Activate data loss prevention (DLP) tools where you have them, and watch for social security numbers, credit card numbers, and other sensitive data patterns.
- Log, alert, and actively investigate any unusual activities on your network or by your staff.
- Get visibility into your cloud Office 365 or Google accounts. Review the intrusion alarms daily.
- Regularly check your network for unauthorized users or connections.
4. RESPOND – have (and regularly test) a plan for:
- Notifying customers, employees, and others whose data may be at risk.
- Keeping business operations up and running (business continuity plan) – include PDF extracts and reports that should be regularly copied up to a secure cloud location.
- Reporting the attack to law enforcement, the state, and other authorities.
- Investigating and containing an attack. Resources here from the U.S. Department of Education (ED).
- Filing with your cyber insurance provider.
- Updating your cybersecurity handbook and disaster recovery plan with lessons learned.
- Preparing for other threats (weather, power, air conditioning) that may put data at risk.
- Managing communications with the parents, community and the press.
5. RECOVER – after an incident:
- Repair and restore the equipment and parts of your network that were affected.
- Keep employees and customers informed of your response and recovery activities.
Resources and References:
- The NIST Cybersecurity Framework
- FTC: Understanding the NIST Cybersecurity Framework
- Introducing the K-12 Cybersecurity Self-Assessment
- How Should We Address the Cybersecurity Threats Facing K-12 Schools?
- ED/PTAC: Security Best Practices
- ED/PTAC: Data Breach Response Checklist
April Mardock has supported cybersecurity and InfoTech in 132 different companies. She is well versed in complex, multilayered environments, and is currently the functional CISO for more than 60,000 users at Seattle Public Schools. She holds a masters in IT and a CISSP security certification, as well as several other industry specific certs. April’s currently responsibilities include site-based technology audits, infosec policy management, disaster recovery and business continuity consulting, firewall management, penetration testing, email spam and web filtering, and on-site network forensics.